Companies tend to focus on the mitigation of malicious outsiders when their own employees pose the greatest financial threat.
- Your partner in video analytics.
- +34 963 123 776
- Contact
- Blog
- Become a Partner

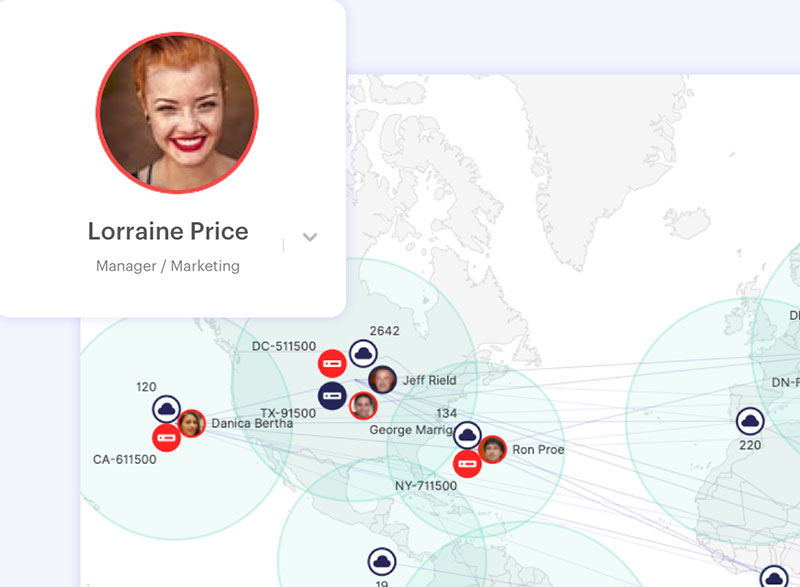
Companies tend to focus on the mitigation of malicious outsiders when their own employees pose the greatest financial threat.
There are various ways employees unintentionally put their organization at risk, including browsing risky websites, downloading malicious files, accessing confidential data through unsecured Wi-Fi networks, or inserting USB sticks containing malware.
From non-malicious to malicious.
From unintentional to intentional.
From the average employee to the tech-savvy IT professional attempting to avoid security controls.
With rich contextual knowledge, you get transparency of the behaviors, actions, and intentions surrounding an incident. Follow a user or file across devices and locations to get the insight you need.
By augmenting the operators, you get actionable alerts, so you can detect and resolve incidents in seconds or minutes instead of days or weeks.
Reveal uniquely combines policies and machine learning sensors to detect and stop more insider risks.
Reveal offers both out-of-the-box and configurable policies that you can customize to align with your security and compliance needs. Policies automate threat detection and response by allowing you to define rules for user activities and the actions that are taken if these rules are breached.
Reveal’s breakthrough machine learning capability combines multiple algorithms that monitor user, entity, and network behavior to detect security threats. The machine learning component generates statistically robust models of behavior that are tailored to each individual in an organization and achieve better predictive performance.
Track file movement on and across systems and browsers with advanced content inspection to protect against data loss. Reveal Agents can inspect files for credit or debit card numbers, identity card numbers, insurance numbers, social security numbers, national health service numbers and more.
With Reveal, employees receive incident-based training that enforces your IT Security Policy and Acceptable Use Policy to align your employees. The instant feedback loop provides effective, time-efficient and affordable security awareness training.
Halt suspicious activity by performing actions on computers. With Reveal, you can isolate devices from the network, lock out user sessions, take screenshots, display messages, block uploads, and kill processes to protect your organization.
Policies are enforced regardless of whether your employees are online, meaning that you can protect your data and devices at all times. This is especially helpful when someone is trying to circumvent security measures.
Reveal ensures incidents are investigated and managed objectively while maintaining user privacy.
Providing anonymization and pseudonymization data masking techniques, Reveal conceals identifying user information so incidents can be analyzed impartially and data protection laws are adhered to.
Understand and transform your security posture with interactive policy violation reporting. The policy reports page lets you view high- and low-level policy sensor data, so you can assess the effectiveness of your existing security controls and identify areas for improvement.
Boost your team’s threat hunting tailored to your specific needs at a fraction of hiring costs with our full-service analysts.

Manage your information security risks within acceptable levels. Prevent data loss or theft of intellectual property, personal data, and financial documents to protect your livelihood and competitive advantage in the market. Ensure compliance with PII, GDPR, NIST, and more while increasing your employees’ security awareness without taking them away from their job with on-screen messages to help train the staff. All included in one tool.

Make your organization’s static IT security policy come to life. With incident-based training and real-time, on-screen messages, you can educate employees to lower the risk of data breaches and ensure compliance without taking them away from their job. Reveal’s cloud-hosted solution is simple to buy, install, and maintain–while reducing overhead. With all features and out-of-the-box protection included, get up and running in no time. Automatic reports help communicate IT security priorities to Management.

Make an impact by working together with IT to protect and equip employees in a cost-efficient and effective manner to meet compliance needs. Raising security awareness reduces risks related to negligent and accidental behavior. Digitally enforce signed documents, such as AUP, ISP, and IP deeds. For off-boarding of staff, take a proactive approach to employees leaving in protecting company intellectual property.
The Microsoft Information Protection (MIP) integration allows customers to sync their sensitivity labels to Reveal DLP policies, so the agents can protect files inside and outside the Microsoft environment.
The Microsoft Outlook integration allows customers to monitor inbound and outbound email activity on the endpoint. Agents can then alert customers to risk indicators and non-compliance, and provide in-situ awareness and training to employees as necessary.
Generate and automatically assign labels to users based on attributes in your LDAP directory. With Reveal’s directory labels, configuration and peer analysts of reports is easier. For example, you can create policies for specific departments, filter policy violation reports by department, and enrich user profiles.
Reveal integrates with IBM’s Qradar to enable security teams to remediate insider risk, whether malicious, negligent, or accidental.
Reveal integrates with Splunk’s analytics-driven SIEM to enhance the team’s ability to detect and respond to endpoint incidents stemming from insiders.
The Slack integration allows line managers, legal, and HR to stay on top of relevant insider incidents when they need to.


Reveal took first place in the insider threat simulation facing seven industry-leading DLP, EDR, UBA, and SIEM vendors. Winner of seven out of ten categories, including best overall performance.

Reveal successfully completed certification testing with the Defense Information Systems Agency’s (DISA) Joint Interoperability Test Command (JITC).

Reveal is compliant with the CNSSD 504 and meets the key User Activity Monitoring (UAM) requirements defined by the NITTF.

Qush won Cyber Security Startup of the Year, exhibiting excellence, strong leadership, evidence of achievement, and innovation to receive this award.

Distinguished vendor with solution to the challenge of supporting the SOC Analysts.
Identify indications of compromise, detect threats, and manage insider risks.
See information flow, identify data exfiltration, and prevent data loss.
Prepare for regulations and security standard audits, ensure compliance in real-time, and lower your risk score.
Autonomously train your workforce on the organization’s information security policy or acceptable use policy.
Secure your organization and its data while enabling employees to perform their duties from home.
The Reveal MSSP Console helps managed security service providers (MSSPs) mitigate insider risks across multiple organizations. With the MSSP Console, you can easily scale your business by managing multiple SaaS deployments from POC to production through a single pane of glass.
Leverage the Reveal MSSP Console to monitor your customers’ environments and in turn mitigate risks, powered by the analytics of Qush Reveal.

The MSSP Console’s intel is powered by the U.S. Cyber Command-winning solution, Qush Reveal. Detect and respond to insider risks across multiple environments, easily diving down into an environment and seamlessly jumping to another.

Certified by the U.S. National Insider Threat Task Force, Reveal and the MSSP Console combine the power of policy and machine learning sensors to protect against malicious, careless, and accidental insider risks.
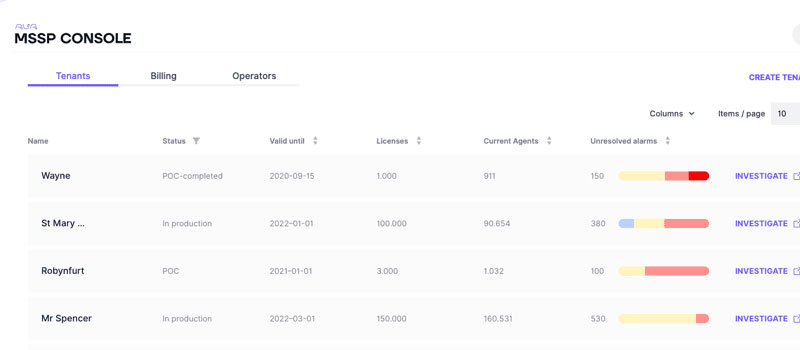
The MSSP Console makes it easy to set up new or manage your existing customers. With a single button, you can dive into each customer’s Reveal deployment.
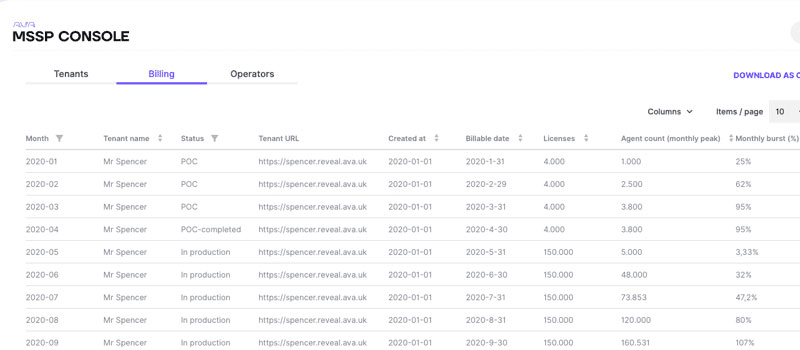
Effortlessly charge your customers using the MSSP Console’s automatic and easy-to-download billing reports. Additional info such as number of agents, commencement date and expiry date is included in the report.

In the vast and risky environment of the oil and gas sector, maintaining strict safety protocols while optimizing operational efficiency is paramount. Here, combining state-of-the-art technology with the specific needs of the industry becomes not only an advantage, but a necessity.
Read more »






















